The new version of the straton software is now available. New features are available like S2 redundancy with ProfinetIO, IEC61850-7-420:2021 compliance of our SCL Editor, new features with TLS like straton T5 protocol security and MODBUS-TCP, WSTRING support and finally a JSON library with additional functional blocks.
Since 2002, we have been committed to our customers’ satisfaction, so we hope that these new features and improvements will help you to meet the challenges of your market. Find a detailed presentation of the main new features of version 12.0 in our release note on YouTube.
Security more and more present in straton
The security of data is always at the heart of the concerns. This year again, we wanted to focus on these features that are so important to you. So we added 2 new protocols to the list of our secure protocols.
Securing the proprietary “T5” protocol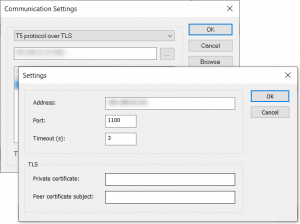
The data exchanges between the editor and the runtime carried by our proprietary protocol “T5” can now be secured. We have added a TLS layer with mutual authentication of certificates. This addition, provided as source code and as an example, will allow you to integrate security more easily in your own systems.
MODBUS-TCP exchanges security
The same applies to MODBUS-TCP connections (Client and/or Server), which can also be secured with TLS thanks to a bidirectional authentication.
At present, the activation of TLS is done directly via the parameters of the fieldbus configurator for the Client, from a configuration file installed with the runtime for the Server.
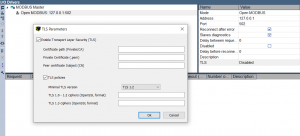
Mutual” (or bidirectional) authentication
By choosing the “mutual” authentication we have chosen a strong security, possible following the authentication of both actors by their partner. In other words, the Client will ask to verify the information on the Server’s security certificate and vice versa.
Alone we go faster, together we go further
Note that the security measures presented above can be combined. It is therefore totally possible to encrypt the exchanges between the editor and the runtime at the same time as the data transmitted by our secure protocols, increasing the overall level of security and at the same time reducing the number of potentially exploitable flaws.






Comments are closed.